Freedom and privacy/security issues
Mobile devices such as phones and tablets are taking and increasingly important part in our computing, hence they are particularly subject to freedom and security concerns. These devices are actually full computers with powerful hardware, running complete operating systems that allow for updates, software changes and installable applications: this makes it easy to run free software on them. Mobile devices are often used for communications and provide hardware features that are sensitive when it comes to privacy and security: GPS, camera, microphone, etc, in addition to storing the user's data. Hence, they are particularly subject to being used to spy on the user.
A simplified overview of mobile devices
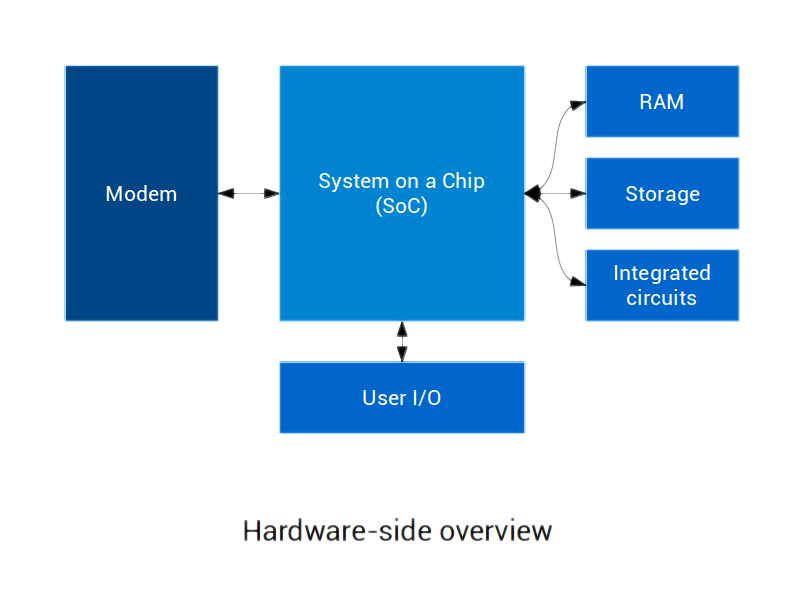 On the hardware side, mobile devices are built with a system on a chip (SoC) that includes a processor (CPU) and various other fundamental components, around which are found various integrated circuits, memory (RAM), storage, user input/output (I/O), etc.
When the device is telephony-enabled, it also features a modem, which is the component in charge of dealing with the mobile telephony network.
This component embeds a powerful processor that runs an operating system, along with dedicated volatile memory. Its storage can be dedicated or shared with the main processor.
On the hardware side, mobile devices are built with a system on a chip (SoC) that includes a processor (CPU) and various other fundamental components, around which are found various integrated circuits, memory (RAM), storage, user input/output (I/O), etc.
When the device is telephony-enabled, it also features a modem, which is the component in charge of dealing with the mobile telephony network.
This component embeds a powerful processor that runs an operating system, along with dedicated volatile memory. Its storage can be dedicated or shared with the main processor.
Regarding the software side of things on mobile devices, the main CPU (inside the SoC) starts by executing hard-wired boot instructions (that cannot be changed), known as the bootrom.
It will look up various places such as NAND, eMMC or MMC (sd/micro sd card) storage, depending on the hardware configuration, to load a bootloader.
The bootloader, which is in fact often split in different stages, is in charge of bringing up and configuring various aspects of the hardware and eventually starting the main operating system by loading and running its kernel.
On some hardware, it is also in charge of loading a privileged execution mode, that runs on the same processor with the highest level of permissions. It might interrupt the system and forbid it from accessing hardware resources. On mobile devices, this is often implemented with TrustZone, where the processor's execution mode is split between a secure world, where the privileged execution mode is running and a non-secure world. The privileged execution mode often keeps running in the background, aside of the main operating system.
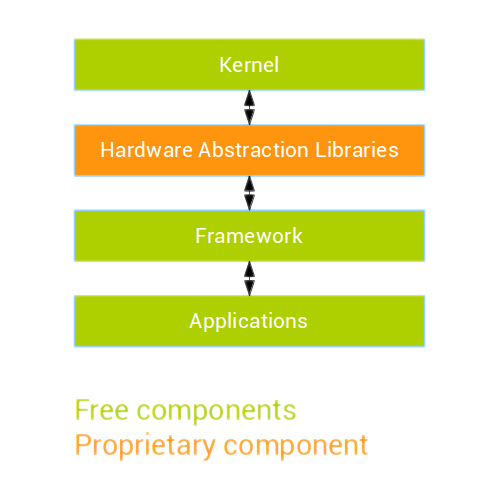
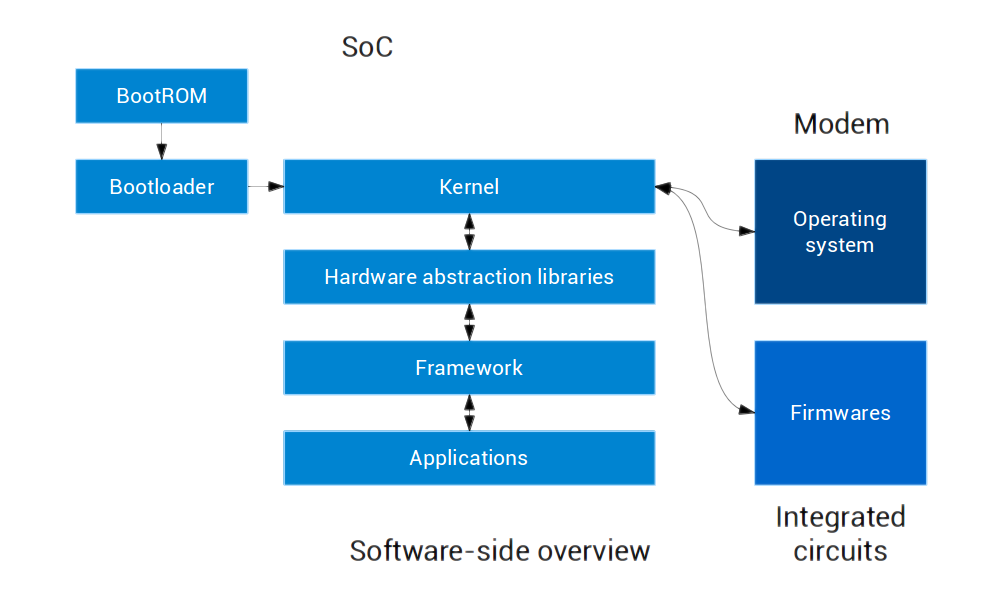 The kernel itself, among other things, deals with the hardware directly and provides ways for other programs (running in user-space) to access it.
In user-space, hardware abstraction layers are programs specific to each device that know how to properly drive the hardware.
They use the kernel to communicate back and forth with the hardware and implement the proper protocols for it.
The kernel itself, among other things, deals with the hardware directly and provides ways for other programs (running in user-space) to access it.
In user-space, hardware abstraction layers are programs specific to each device that know how to properly drive the hardware.
They use the kernel to communicate back and forth with the hardware and implement the proper protocols for it.
The actual knowledge of how to drive the hardware is split between the kernel and the hardware abstraction layer libraries: both are needed to make it work properly.
Hardware abstraction layers provide a generic interface for the framework to use.
The framework itself provides an interface for applications that is independent of the device and the hardware.
That way, applications can access hardware features through the generic framework interface, which will call the hardware abstraction layer libraries, ending up with the kernel communicating with the hardware.
For instance, when placing a call, the dialer application will communicate with the framework, which in turn will communicate with the hardware abstraction layer.
That hardware abstraction layer will implement the protocol to communicate with the modem. The kernel will then forward the communication between the hardware abstraction layer and the modem.
Many other components of a mobile device also run software in different forms. The various integrated circuits run small pieces of dedicated software that are called firmwares. When the device is telephony-enabled, there is also software running on the modem. Modern modems are complex and run full operating systems.
The current situation of freedom and privacy/security on mobile devices
A mobile device respecting the users' freedom would have:
- Free hardware
- Free firmwares
- Free modem system
- Free bootrom and bootloader
- Free system and applications
Logic configuration used in programmable logic devices such as FPGAs exists with free licenses. However, these logic devices are not practical enough to replace dedicated integrated circuits (ASICs) in smartphones and most of them require proprietary toolchains.
Firmwares running inside integrated circuits are most of the time proprietary. While free firmwares are hard to write, some exist for very specific hardware (e.g. Arduino, Bus Pirate) and sometimes, manufacturers can liberate firmwares running in their integrated circuits (e.g. ath9k_htc). However, it is not always possible to even replace those firmwares: some are loaded to the integrated circuit by the main CPU, but some others reside in separate storage from where they are loaded by that integrated circuit. With separate storage, it can be difficult (to impossible) to update the firmware to a free replacement.
 The modem system on telephony-enabled mobile devices is always proprietary.
While OsmocomBB, a free software GSM stack exists, it only runs on some old feature phones, or on the modem used in the Openmoko phones.
It currently requires a host computer to operate and is not certified to run on public networks.
Despite this situation, the modem remains a crucial part for privacy/security: it is nearly always connected to the GSM network, allowing for remote control.
The modem can be more or less damaging to privacy/security depending on what hardware it has access to and can control.
That is to say, how isolated it is from the rest of the device.
The modem system on telephony-enabled mobile devices is always proprietary.
While OsmocomBB, a free software GSM stack exists, it only runs on some old feature phones, or on the modem used in the Openmoko phones.
It currently requires a host computer to operate and is not certified to run on public networks.
Despite this situation, the modem remains a crucial part for privacy/security: it is nearly always connected to the GSM network, allowing for remote control.
The modem can be more or less damaging to privacy/security depending on what hardware it has access to and can control.
That is to say, how isolated it is from the rest of the device.
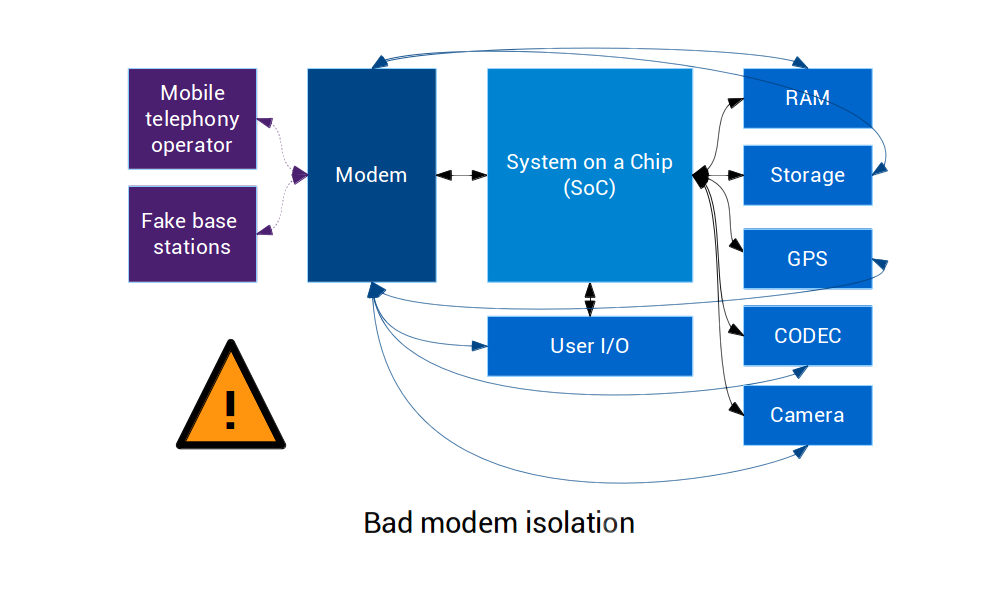
A device with bad modem isolation cannot prevent the modem from accessing and controlling key parts of the hardware.
For instance the main CPU's RAM, its storage, the GPS, the camera, user I/O and the microphone.
This situation is terrible for privacy/security as it provides plenty of opportunities to efficiently spy on the user, that could be triggered remotely over the mobile telephony network.
That mobile telephony network is accessible to the mobile telephony operator, but also to attackers setting up fake base stations for that purpose.
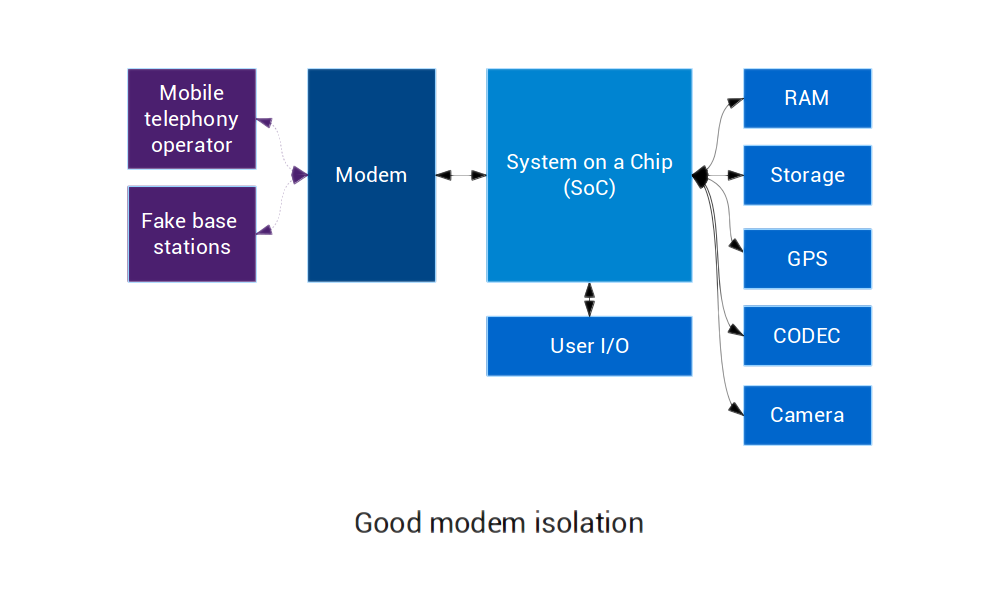 On the other hand, when the modem is well-isolated from the rest of the device, it is limited to communicating directly with the SoC and can only access the device's microphone when allowed by the SoC.
It is then strictly limited to accessing what it really needs, which considerably reduces its opportunities to spy on the user.
While it doesn't solve any of the freedom issues, having an isolated modem is a big step forward for privacy/security.
However, it is nearly impossible to be entirely sure that the modem is actually isolated, as any documentation about the device cannot be trusted, due to the lack of effective hardware freedom.
On the other hand, it is possible to know that the modem is not isolated, when there is proof that it can access hardware that could be used to spy on the user.
On the other hand, when the modem is well-isolated from the rest of the device, it is limited to communicating directly with the SoC and can only access the device's microphone when allowed by the SoC.
It is then strictly limited to accessing what it really needs, which considerably reduces its opportunities to spy on the user.
While it doesn't solve any of the freedom issues, having an isolated modem is a big step forward for privacy/security.
However, it is nearly impossible to be entirely sure that the modem is actually isolated, as any documentation about the device cannot be trusted, due to the lack of effective hardware freedom.
On the other hand, it is possible to know that the modem is not isolated, when there is proof that it can access hardware that could be used to spy on the user.
Looking at the software that runs early on the SoC, the first component is the bootrom. It is always proprietary and is stored in read-only memory, so it cannot be changed (in that case, it almost seems to behave like hardware). However, regarding the bootloader, the situation is different for each platform. There are actually multiple stages of bootloaders, some of which can be free. However, it also occurs that the bootloaders are cryptographically signed with a private key. In that case, the bootrom will check the signature against a public key that cannot be replaced and only run the bootloader if the signature matches. That sort of tivoization prevents replacing pre-installed bootloaders, even when their sources are released as free software. This is even more problematic when the bootloader is in charge of loading code in privileged execution mode as it gives full control of the processor to software that is proprietary and/or cannot be modified. There are some good platforms that don't perform such signature checks and can run free bootloaders (e.g. Allwinner Ax, TI OMAP General-Purpose).
 The biggest part of the software running on a mobile device is the main operating system, that runs on the main CPU.
It has access to most integrated circuits (I/O, camera, microphone, GPS, etc) as well as the user's data and communications.
It is the most critical part for privacy/security and is also very important for free software as it interacts with the user directly and holds knowledge about communication with the hardware.
Many mobile operating systems are mostly free software (e.g.
Android, Firefox OS, Ubuntu Touch, Tizen), as they use the Linux kernel, a free framework and ship with free base applications.
However, the user-space hardware abstraction layers are for the most part proprietary (it varies from one device to another) and they also ship with proprietary loaded firmwares for various integrated circuits.
Every piece of proprietary software running on the system is a risk for privacy/security as they can offer remote access back-doors and compromise the rest of the system.
The biggest part of the software running on a mobile device is the main operating system, that runs on the main CPU.
It has access to most integrated circuits (I/O, camera, microphone, GPS, etc) as well as the user's data and communications.
It is the most critical part for privacy/security and is also very important for free software as it interacts with the user directly and holds knowledge about communication with the hardware.
Many mobile operating systems are mostly free software (e.g.
Android, Firefox OS, Ubuntu Touch, Tizen), as they use the Linux kernel, a free framework and ship with free base applications.
However, the user-space hardware abstraction layers are for the most part proprietary (it varies from one device to another) and they also ship with proprietary loaded firmwares for various integrated circuits.
Every piece of proprietary software running on the system is a risk for privacy/security as they can offer remote access back-doors and compromise the rest of the system.
None of these mostly-free systems have a clear policy to reject proprietary software and not advocate its use, except for Replicant.
While the main operating system is a very important piece of software, it doesn't ship with applications that cover the wide spectrum of activities that a mobile device is expected to provide. Thankfully, plenty of free software applications exist for each kind of (mostly-)free operating system, sometimes gathered in free software application stores (such as F-Droid for Android systems).
Mobile telephony operators and privacy
Even though telephony-enabled mobile devices hold a tremendous potential for spying on the user, they are not the only tools that can be used to spy in the mobile world. Most mobile telephony operators keep track of every message and call made by the user but also gather the real time position of users, filter their mobile data networks and provide security agencies unlimited access to that data, to an extent that depends on the operator, the country and the government.
As these issues are fundamentally political and not technical (even though technical workarounds are possible in some cases), the proper way to solve those is to demand progress and take political action. It is especially important as the tendency for governments is to worsen the situation by allowing more and more tracking and spying on the users.
Recommendations
Given the current situation, there is no ideal device available that would satisfy all the requirements to fully respect users' freedom: hardware freedom is missing and most firmwares, modem operating systems and bootroms are non-free. However, it is possible to choose a device that runs with free bootloaders and a free mobile operating system: Replicant, as well as free applications.
Privacy/security cannot be reliably achieved, but it is possible to get close to it by choosing a device that is not proven to have bad modem isolation, provides a reliable way of deactivating the modem or doesn't feature any modem at all, in addition to running software that is as free as possible and following some general good advice.
Choosing the best Replicant-supported device
Each device comes with its own share of freedom and privacy/security-related problems, that are detailed on the devices' wiki pages. Among the devices that Replicant supports, some perform better than others when it comes to free software support and modem isolation.
Replicant-supported phones recommendations:
- The GTA04 should be the preferred choice as it can run Replicant with free bootloaders and was not proven to have bad modem isolation: instead, the documentation about the hardware indicates very strong modem isolation. The GTA04 is not fully supported by Replicant yet but we are currently working to improve the situation.
- Second choices include the Galaxy S 2 (GT-I9100), the Galaxy S 3 (GT-I9300), the Galaxy Note 2 (GT-N7100) and the Galaxy Nexus (GT-I9250), in order of supported hardware features in Replicant (more to less). These devices are fairly common and easy to find. They do not run free bootloaders, but were not proven to have bad modem isolation and perform well with Replicant.
Replicant-supported tablets recommendations:
- The Galaxy Tab 2 7.0 (GT-P31x0) is the preferred choice for a tablet. It is fairly common and easy to find. However, it does not run a free bootloader. It exists in a Wi-Fi-only version and the version featuring a modem was not proven to have bad modem isolation.
General good advice for freedom and privacy/security
Some general good advice to ensure the best possible respect of freedom and privacy/security on mobile devices includes:
- Installing only free software applications, from trusted sources such as F-Droid on Replicant.
- Encrypting the device's storage with a strong passphrase, to prevent some unauthorized access to the device's data.
- Using software that provides secure encrypted communications such as Conversations for instant messaging and OpenKeychain with K-9 Mail for emails on Replicant.
- Using Tor to achieve reliable anonymity, for instance with Orbot on Replicant.
- Using Silence to encrypt SMS messages.
- If the device is telephony-enabled, switching the modem to airplane mode or (when possible) turning it off when not in use, to avoid being tracked at all times.
- Browsers using the webview framework (such as the browser shipped with Replicant and Lightning) are subject to various security flaws in Replicant 6.0. Replicant 4.2 did not receive security updates since its latest release in September 2015 and many serious security issues are not fixed.
Notes
Free hardware refers to hardware that allows the same four essential freedoms that free software describes, transposed to hardware. Roughly, it means that the users have the freedom to use, duplicate, distribute, study, change and improve the hardware and its design. The equivalent of source code for hardware would be the hardware design source, in the form of schematics, implementation designs or hardware description language sources that could be used to produce the hardware from scratch. It is the preferred source for hardware designers to describe the hardware.
Such a transposition of the four essential freedoms of free software to hardware could be:
- The freedom to use the hardware, for any purpose.
- The freedom to study how the hardware works, and change it so it works as you wish. Access to the hardware design source is a precondition for this.
- The freedom to redistribute copies of the hardware and its design so you can help your neighbor.
- The freedom to distribute copies of your modified versions to others. By doing this you can give the whole community a chance to benefit from your changes. Access to the hardware design source is a precondition for this.

